Installing Ubuntu 14.04 on a 15" late 2013 Macbook Pro (with Full Disk Encryption)

SO I've been looking but I have yet to find a sufficiently detailed guide for getting Ubuntu running on a retina macbook pro, especially one that has full disk encryption enabled. Hopefully this document will help others looking to dual boot as well as serve as a reference for me in the future when I inevitably forget all of this.
BEFORE YOU DO ANYTHING YOU NEED TO HAVE A BACKUP!
The first step was installing a better EFI boot loader (although I'm not sure if this step is strictly necessary anymore). In the past that would involve rEFIt, but it seems to have lots its maintainers. Instead I've gone with rEFInd. Their site is pretty 1990s, but the software itself is pretty good. I mostly just followed the instructions on their installation page and their page on Yosemite, although I did have to make a few changes so that booting wouldn't take 30 extra seconds. Note, I had to install rEFInd to my ESP partition
- First step is to download rEFInd (version 0.8.3 as of this article) and unzip it somewhere.
- Now mount the ESP partition by making a new directory ( mkdir /Volumes/esp ) and then running: sudo mount -t msdos /dev/disk0s1 /Volumes/esp
- Next cd into the directory you unzipped rEFInd and run ./install.sh --esp
- Now edit /Volumes/esp/EFI/refind/refind.conf and uncomment the line about dont_scan_volumes and change it to be dont_scan_volumes "foo,bar"
- Next move /Volumes/esp/EFI/refind to /Volumes/esp/EFI/BOOT
- Finally move /Volumes/esp/EFI/BOOT/refindx64.efi (I think) to /Volumes/esp/EFI/BOOT/bootx64.efi
- REBOOT and enjoy your shiny FOSS boot manager
The next step is to format your hard drive so that it has 3 new partitions for Ubuntu. I like to use full disk encryption in linux too which means that I need a separate /boot partition in addition to / and swap (although frankly I'm not sure I need swap when I have 16GB of RAM)
BE CAREFUL HERE. I managed to bork my Mac installation by trying format my disk from the ubuntu live CD. Thankfuly I had a time machine backup.
I ended up formatting my disk to my liking by booting in to OS X's recovery mode and creating 3 new partitions. My /boot was only 1GB, swap was 16GB and I set aside about 90GB for the main installation.
Next you need to format a USB stick with the ubuntu installation image. The instructions I followed are from here: http://www.ubuntu.com/download/desktop/create-a-usb-stick-on-mac-osx
Reboot with your newly formatted USB and select it from the options presented.
Choose 'Something else' when asked how to install ubuntu. Click on the 1 GB partition and use it as /boot. Next choose the large partition you created for linux and choose the option "use as physical volume for encryption"
Also, make sure you choose the partition you have as /boot for the installation of the boot loader. YOU DO NOT WANT TO LEAVE IT AT ITS DEFAULT
Next post I'll include information on how to configure your new dual boot computer!
Intro to Kerbal Space Program!
So I’ve discovered an another awesome sandbox game! I really thought I didn’t like them, but I was wrong. Trying to build space ships is fun! If you succeed, you get to go to space! If you fail things explode in amusing ways! Bonus, you’re some kind of magic god in the game so you can roll back time and make the explosion never happen!
My only complaint so far has been just how obscure the UI can be… obscure. You have to click or double click or right click or possibly even double right click on exactly the right part of your ship in order to get a menu to show up...
The best guide I’ve read so far is found here: http://mykspcareer.com/2014/07/volume1/
The best part of this game though is just how cool I feel while playing! Who doesn’t want to feel like a rocket scientist? It feels really cool to understand how orbital mechanics work.
BONUS: Awesome ships I’ve made!

I found it is IS possible to build a plane capable of taking off without wheels

Solution to 1o57's Hackaday Challenge
So on October 6th 1o57 (who creates the DEF CON badge challenge) gave a fantastic talk at the hackaday 10th anniversary which you should totally watch:
(go ahead, I’ll wait)
You might have noticed some random text in the slides, but you might not have. Anyway here are the slides
@hackaday pic.twitter.com/YNNoeJDeSU
— LosT/李智上 (@1o57) October 5, 2014
@hackaday pic.twitter.com/YNNoeJDeSU
— LosT/李智上 (@1o57) October 5, 2014
@hackaday pic.twitter.com/ss3WEzndR9
— LosT/李智上 (@1o57) October 5, 2014
@hackaday pic.twitter.com/NVxwlBEe2y
— LosT/李智上 (@1o57) October 5, 2014
@hackaday pic.twitter.com/oE64HPUqtx
— LosT/李智上 (@1o57) October 5, 2014
@hackaday pic.twitter.com/LMXhiJj5mu
— LosT/李智上 (@1o57) October 5, 2014
@hackaday pic.twitter.com/Tb42KBb8bl
— LosT/李智上 (@1o57) October 5, 2014
@hackaday pic.twitter.com/UhXCk0tyLX
— LosT/李智上 (@1o57) October 5, 2014
@hackaday pic.twitter.com/bIDNsV3D5g
— LosT/李智上 (@1o57) October 5, 2014
@hackaday pic.twitter.com/zqarmBmwNd
— LosT/李智上 (@1o57) October 5, 2014
And here is a copy of all the letters on each of the slides
DO
XIYL
DCYV
DKIK
NKUM
KRYD
NBYG
ONYM
NXOC
on one line:
DOXIYLDCYVDKIKNKUMKRYDNBYGONYMNXOC
Hrmmm, well the first thing you might try is a Caesar cipher. In the video you’ll notice that 1o57 repeatedly mentions that it’s Hackaday’s TENTH anniversary, so we should try decrypting the above string with a key of 10. (here’s a tool do to that)
TENYOBTSOLTAYADAKCAHOTDROWEDOCDNES
(side note: I cheated on this step by using an automated caesar cipher breaker)
Hrmmm that still looks like nonsense, but it does start with the word ten, so we’re probably close...
Wait a second! The string is backwards! It’s not ten it’s net!
SENDCODEWORDTOHACKADAYATLOSTBOYNET
or cleaned up
Send codeword to hackaday@lostboy.net
Ok, well now we know where to send the codewords. The only unsolved part of the puzzle is this last slide
@hackaday pic.twitter.com/01Magsvu1u
— LosT/李智上 (@1o57) October 5, 2014

WTF are those things?! Now fans of Sherlock Holmes may recognize these, but at the time I did not, so I went to my best friend Google to try and figure it out. I tried lots of search terms like “stickman code" (and variants on that) and “semaphore" (since I thought maybe the positions on the flags was significant), until I came across this page:
http://www.geocachingtoolbox.com/index.php?lang=en&page=dancingMen
which features a code called the Dancing Men!
This code comes from a Sherlock Holmes novel called The Adventure of the Dancing Men
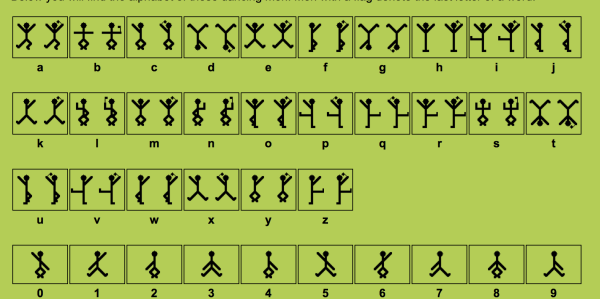
And we can use the above image to decrypt the band, which decrypts to:
codeword psychobilly ciphers
Thanks for the fun puzzle 1o57!
NIXIE TUBES!!
So approximately 2000 years ago I got a set of 6 nixie tubes as a gift. WTF is a nixie tube you ask? This is a nixie tube:

It’s an device for displaying all ten digits (0 through 9) using “glow discharge" (that thing that makes old incandescent lightbulb works), while looking really really cool.
The tubes I have are IN-17s and they operate at 180V. That is a lot of volts and it was pretty scary for me putting the circuit together since I’ve never worked with such high voltages. Fortunately, these works at relatively low amperages so I only have to worry about pain, not death.
Now, you might be wondering what I need to drive these things. The answer would be a Russian K155NA1 Driver Chip, which is basically a high voltage Binary-Coded Decimal decoder and a circuit to step up wall wart DC voltage (9V at 1a) to 180V. Thankfully a nice person on the internet made an arduino shield to do all this called the ArduiNIX
Here’s my completed display:
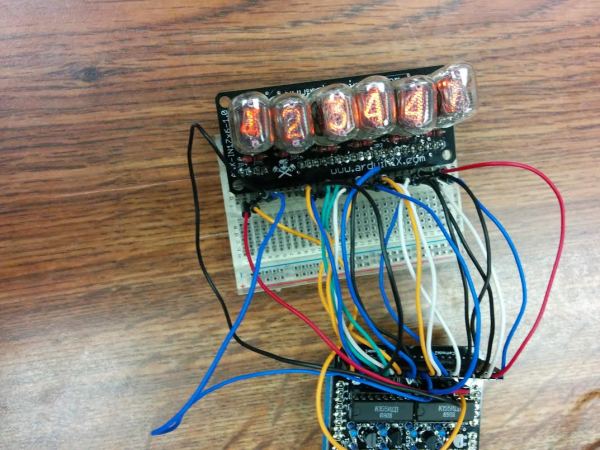
I’m still trying to understand how the circuit works. There are 20 pins and 4 grounds, so I can apparently control a total of 80 digits. I’m only using 60 digits in this setup (10 digits per tube times 6 tubes), but I’m still pretty lost when reading the demo code
My current understanding is that I have 2 BCDs which I can control with 8 pins (4 each, which makes sense since 2^4 = 16 > 10 digits), and I can control the 4 anode (aka ground) pins. From the code it seems I have to display 2 digits at a time, but I’m not at all clear how the digits are split up. That will be the subject for my next post!
SHELL SHOCKED
There's a lot of chatter right now about this new bash env bug, affectionately known as CVE-2014-6271. I'm going to try and explain for your (but mostly my own) benefit.
BACKGROUND
The primary way that programmers interact with a (un|l)inux system is via the shell, aka THE COMMAND LINE (cue thunder clap)
Now, like everything on a computer, the shell is a program. It's kinda special since it runs OTHER programs. It's not just users who use it, but also other commands.
In bash, there's these things called **environment variables**, which is a way to declare values which can be used by scripts/programs to store variables. A common shell variable is LANG, which contains the current users language. A program launched from the shell can use this information to display output in the correct language.
Bash is also a self contained programming language, and like any good programming languge it has functions. You can declare functions in bash like so
foo() {
echo 'bar';
}
Seems pretty straight forward right? The key is that bash stores functions that it is exporting to another bash shell using environment variables.
Only there's a bug in bash which means that once a function is parsed, bash happily keeps executing the rest of the environment variable.
THE ACTUAL PROBLEM
Ok, so what does that look like? You can normally declare an env variable like so:
bar='something important'
You can declare a function in an environment variable like so:
foo='() { echo 1;};'
And the exploitable version is like this:
x='() { ignored;}; echo vulnerable' bash
The x='() { :;}; bit is just to ensure that bash parses this environment variable like a function. After the second semi-colon, you can execute any bash you want.
WHY THIS IS BAD
What's the big deal you ask? I don't let random internet strangers set environment variables! Well, you might be doing it without realizing it. The first series of exploits that can be taken advantage of right now is CGI.
CGI lets you execute a shell script of any kind to respond to a web request. The problem is that if you are using a bash script, cgi helpfully sets the user agent of the request it is trying to process to an environment variable! This means that by doing
curl -A "() { :;}; whoami" http://some.vulnerable.computer/cgi-script
You can execute code
The second class of attacks that is interesting is that there are lots of ssh systems that provide access, but don't give the end user a shell. The most common case of this is with git, where users exist on a system for execution, but ssh is configured not to respond with a shell. A user without a shell account (but with access) can login to ssh like so:
ssh -o 'rsaauthentication yes' user@host.me '() { ignored; }; /usr/bin/whoami'
The final interesting class of attacks is with dhclient. Now, when you connect your computer to a network, it sends a request out to EVERY computer asking for an IP address. Normally a DHCP server would respond to this request, and this response is used to set some environment variable before a shell script is run on the requester's machine to set ip addresses and such what. The problem here is that a malicious user could respond faster than a real DHCP server with a response that contained fields which would be put into environment variables and then GAME OVER.
subscribe via RSS